Source: Chainalysis; Translated by Deng Tong, Golden Finance
In 2024, the ransomware landscape underwent major changes, and cryptocurrencies continue to play a core role in ransomware. However, the total ransom amount fell by about 35% year-on-year due to increased enforcement actions, improved international cooperation and an increasing number of victims’ refusal to pay.
In response, many attackers have changed their strategies, with new strains of ransomware emerging from renamed, leaked or purchased code, reflecting a more adaptable and agile threat environment. Ransomware operations also get faster, and negotiations usually begin within hours of data breaches. Attackers include actors, ransomware as a service (RaaS) operations, individual operators, and data theft ransomware groups, such as those who ransom and steal data from cloud service provider Snowflake.
In this chapter, we will explore these developments and their implications, including a variety of case studies — LockBit, Iranian ransomware strains, Akira/Fog and INC/Lynx — to reflect the trend this year.
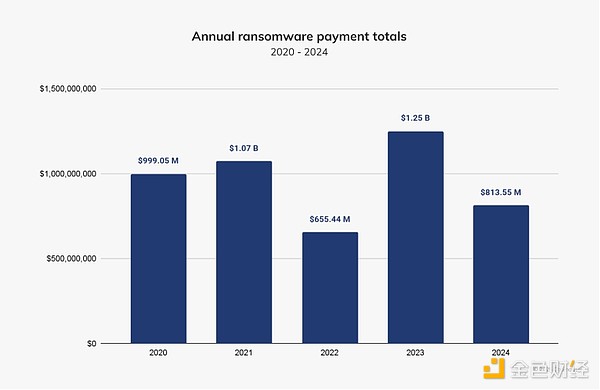
Ransomware activity shifted mid-yearIn 2024, ransomware attackers received about $813.55 million in payments from victims, down 35% from the record $1.25 billion in 2023, which This is the first time that ransomware revenue has dropped since 2022.
As we pointed out in the mid-year crime update, ransomware attackers ransomware attackers have reached $459.8 million between January and June 2024, compared with 2023 The amount of ransomware during the same period was about 2.38%. There were also several unusually large payments in the first half of 2024, such as a record $75 million payment to Dark Angels.
Although the total in 2024 showed a small half-income growth (HoH), we expect to exceed the total in 2023 by the end of the year. Fortunately, payment activity slowed by about 34.9% after July 2024. This slowdown is similar to the decline in half of ransom payments since 2021 and the overall decline in certain types of crypto-related crimes such as stolen funds in the second half of 2024. It is worth noting that the decline this year is more obvious than in the past three years.
A careful study of the top 10 revenue-ranking ransomware strains in the first half of the year can give you an in-depth look at the groups driving these HoH trends. As shown in the figure below, Akira has launched attacks on more than 250 entities since March 2023, the only one among the top 10 ransomware strains in the first half of the year to step up its efforts in the second half of 2024. LockBit was first aged by the UK Crime Agency (NCA) and the United States Federal in early 2024The Bureau of Investigation (FBI) disrupted, and its payments fell by about 79% in the second half of the year, demonstrating the effectiveness of international law enforcement cooperation. ALPHV/BlackCat, once one of the highest-paid strains in 2023, withdrew in January 2024, leaving a gap in the second half of the year.
Lizzie Cookson, senior director of incident response at ransomware incident response company Coveware, told us: "After LockBit and BlackCat/ALPHV collapse, the market has never returned to its former state. We've seen a solo act of action. But we haven't seen any group absorb their market share quickly, as we've seen after the previous high-profile demolition and closure. The current ransomware ecosystem is filled with many newcomers who tend to Focusing on small and medium-sized markets, which in turn are related to more moderate ransom requirements. ”
To further understand the reasons for the reduction in ransomware payment activity in the second half of the year ,We first looked at the data breach websites that may be representatives of ransomware incidents. In the figure below, we can see that the number of ransomware incidents increased in the second half of the year, but the on-chain payments decreased, which indicates that the number of victims increased, but the amount paid decreased.
The data breach website released more victims than in any previous year. Not only are there more so-called victims, but there are 56 new data breaches sites in 2024 — more than double the number of Recorded Future discovered in 2023, according to Recorded Future threat intelligence analyst Allan Liska. However, there are some considerations to consider for data breaching website information and its implications for the ransomware ecosystem.
eCrime Threat Researcher Corsin Camichel shares more information about the legality of leaks. "We observed leaked website posts claiming that the organization exists, but failed in a deeper analysis. For example, we saw statements from multinational organizations, but in reality, only one smaller subsidiary was affected. In 2024, More than 100 organizations are listed on two or more data breach sites. 'MEOW' leaked sites play an important role in it, appearing to destroy the site and list the data obtained from the web server or database. "The above ransomware Another reason for the inverse relationship between software payments and data breach website victims may be that threat actors are found to exaggerate or falsely report victims or repost claims from old victims. “LockBit operators play tricks after an enforcement action called ‘Operation Cronos’, pretending to remain relevant and active as they republish many of the previously listed claims again,Or added attacks that occurred long ago, some even a year ago,” Camichel added.
Liska also shared with us about illegal victims posted to the data breach website, And said: “This is especially true for LockBit, which, after being excluded by many underground communities after the enforcement action, has posted up to 68% of victims of duplication or direct fabrication on its data breach website. ”
After the LockBit interruption and BlackCat exit scam, another interesting phenomenon is the rise of RansomHub RaaS, which absorbs a large number of displaced operators from LockBit and BlackCat. According to Camichel, RansomHub is in 2024 The largest number of victims in the year, although it only appeared in February 2024, it ranked among the top ten crime types in 2024, according to on-chain data.
Incident response data shows that the amount requested and the amount paid The gap between the two factors continues to widen; in the second half of 2024, the difference between the two factors is 53%. The incident response company report shows that most customers choose not to pay at all, which means the actual gap is greater than the figures below Let's be bigger.
We interviewed Dan Saunders, EMEA Incident Response Director, Kivu Consulting, a cybersecurity incident response company, to learn more about this type of victim resilience. "According to our data, about 30 % negotiations end with payment or victim decision to pay the ransom. Often, these decisions are based on the perceived value of the data being leaked,” he said. Similarly, Cookson notes that victims are increasingly able to resist requests and explore recovery from attacks due to improved cyber hygiene and overall resilience. "They may end up thinking that decryption tools are their best choice and negotiate to reduce final payments, but more commonly, they find that recovery from recent backups is a faster and more cost-effective way to do so, ” she added. Regardless of the initial requirement, the final payment amount is usually between $150,000 and $250,000.
From the image below we can see the evolution of ransomware payment distribution in 2024. In 2020, ransomware payments had a long tail but only a peak, but in 2024, ransomware participants were divided into three categories. Some ransomware participants, such as Phobos, had an average payment of less than $500 to $1,000. Also One cluster is around $10,000, and the third cluster pays over $100,000, some of which hit $1 million. We also see more events at the high end of the distribution, which means more thanThe attack rate of $1 million is even greater.
This breakdown reflects the changes in the ransomware participant landscape observed by Cookson, where smaller groups dominate low- and medium-value payments, while anomalies of 7-8-digit ransoms will be distributed Push right to the third category of payments.
In the figure below, we can see what pressures are in terms of the total ransomware value (bubble size), median payment scale (X-axis), and ransomware event index (Y-axis) It's the worst.
Ransomware outflow: Where did the funds go?Understanding ransomware money laundering methods can provide important insights into the behavior of post-vulnerability threat actors, allowing law enforcement to respond more effectively and in some cases predict future actions based on established patterns.
In the figure below, we see that ransom funds are mainly through centralized exchanges (CEXs) (for capital outflows), personal wallets (for holding funds), and bridges (trying to cover up capital flows). We have noticed that the use of coin mixers has dropped significantly in 2024. Historically, currency mixing services typically account for 10% to 15% of ransomware’s quarterly money laundering traffic. Over the years, the reduction in hybrid services among ransomware participants has been very interesting and demonstrated the destructive impact of sanctions and enforcement actions, such as those against Chipmixer, Tornado Cash and Sinbad. We note that ransomware participants are increasingly relying on cross-chain bridges to replace currency mixers to facilitate their outflow of funds. By contrast, CEX remains a mainstay of ransomware money laundering strategies, with reliance on such services slightly above average in 2024 (39%, compared to 37% in the 2020-2024 period).
It is worth mentioning that a large amount of funds are stored in a personal wallet. Strangely, ransomware operators are a largely economically driven group that are less willing to cash out than ever before. We believe this is mainly due to unpredictable and decisive actions taken by law enforcement against individuals and services involved in or assisting ransomware money laundering, resulting in threat actors feeling unsafe about the safe place for funds to be stored.
While there may be multiple factors behind any trend in the picture above, the decline in KYC usage since October 2024 may be attributed to The designation of the Russian exchange Cryptex and the German Federal Criminal Police Agency (BKA) have seized 47 Russian-language KYC cryptocurrency exchanges – both actions occurred in September 2024. The time of these enforcement actions, coupled with the period when ransomware flows into KYC-free exchanges, is evident.
Ransomware Case Study Panev's arrest and its impact on LockBit operationsIsse from 2019 to 2024Rostislav Panev, a dual nationality of column and Russia, allegedly played a key role in supporting LockBit. He was accused of developing several tools for the group, one of which enables an attacker to print ransom orders from any printer connected to an infected system, and he reportedly received about $230,000 in Bitcoin (BTC) for this. . While Russia, including LockBit administrator Dimitry Yuryevich Khoroshev, has been previously sanctioned for participating in these attacks, it is important to recognize that ransomware is indeed a global threat involving participants from all over the world. Panev, who is currently awaiting extradition to the United States in Israel, is wanted for conspiracy to commit fraud, cybercrime, telecom fraud and other crimes.
In the Reactor chart, we can see that, according to the indictment, about $5,000 of BTC has been transferred from Khoroshev every two weeks starting in 2022. Then, from July 2023 to early 2024, about $10,000 of BTC per month was transferred to Khoroshev.
Panev's arrest could have a major blow to LockBit's restructuring capabilities, stressing that even after years of crime, the transparency and immutability of blockchain still make it Law enforcement can track illegal activities and combat transnational cybercrime groups. LockBit’s outlaw and Panev’s arrest were a major victory in 2024 and triggered a shift to a more fragmented and less coordinated ecosystem.
Iranian ransomware participationIn addition to Russian-speaking cybercriminals, Iran has also been under the Office of Foreign Assets Control (OFAC) of the U.S. Treasury for its participation in assisting and carrying out ransomware attacks in the past few years Sanctions. We also noticed on-chain evidence that LockBit affiliates work with Iranian ransomware strains and deposit funds on Iran’s exchanges.
Luckily, through our on-chain analysis, we can identify Iranian participants as they are rebranding or moving to a different RaaS. As we see in the Chainalysis Reactor chart below, we associate four different ransomware strains with the same Iranian threat actor, who most likely deployed a popular RaaS strain as well. We also see deposit addresses being reused on multiple global exchanges, linking these seemingly different strains – not only connecting with each other, but also confirming the operator’s relationship with Iran.
Main ransomware renamed, branching outSince Akira's emergence, it has been proven to be able to successfully exploit vulnerabilities (especially in enterprise environments) and through a series of pipingThe attention-grabbing attacks gained attention. As we mentioned above, Akira is the only top 10 ransomware to step up its efforts in the second half of 2024.
In September 2024, a new ransomware Fog entered the scene and has since shown a very similar ability to target critical vulnerabilities as Akira. The two organizations focus primarily on exploiting VPN vulnerabilities, which enables them to access the network without authorization and thus deploy ransomware.
Akira and Fog both use the same money laundering method, which is different from other ransomware, further supporting their connection. For example, the following Chainalysis Reactor chart shows that several wallets operated by Akira and Fog have transferred funds to the same KYC-free exchange.
In addition to Akira’s relationship with Fog, we also discovered the link between INC and Lynx ransomware variants by examining similar on-chain behavior. Cybersecurity researchers also noticed that the two variants share source code.
These overlapping relationships illustrate a broader trend in the ransomware ecosystem: cybercrime strategies are evolving in response to increased scrutiny by law enforcement.
Responding to changing threat situationsRansomware in 2024 reflects changes driven by law enforcement actions, increased victim resilience, and emerging attack trends. Crackdown operations and collaboration with incident response companies and blockchain experts help dismantle many ransomware groups and reduce their profitability. The victims also showed greater resistance to ransom demands, thus widening the gap between ransom demands and payments.
Amid law enforcement pressures, financial strategies continue to adapt, although malicious actors face increasing difficulties in money laundering. Continuous collaboration and innovative defensive measures remain critical to consolidating progress made in 2024.











