Last week, we released the 2024 Blockchain Security and Anti-Money Laundering Annual Report produced by SlowMist. Next, we divided the report into four articles to interpret and analyze the report. The key content helps readers gain a more comprehensive and in-depth understanding of the key security challenges and opportunities in the current blockchain ecosystem. This article mainly focuses on the blockchain ecological security situation.
In the security field, 2024 will continue the severe situation in the past. Hacker attacks occur frequently, especially attacks on centralized platforms that dominate. At the same time, smart contract vulnerabilities and social engineering attacks are still the main means of evil for hackers, while phishing attacks are more subtle and complex, and the protection of user assets still faces major challenges. Supply chain security issues have also attracted more attention in 2024, with multiple well-known projects encountering malicious code injection attacks, resulting in the loss of a large number of user assets.
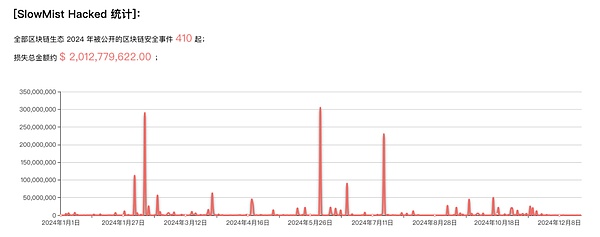
According to statistics from the SlowMist Hacked event archive, a total of 410 security incidents occurred in 2024, with losses as high as US$2.013 billion. Compared with 2023 (a total of 464 cases, losses of approximately US$2.486 billion), losses decreased by 19.02% year-on-year.
Note: The data in this report are based on the token prices at the time of the event. Due to currency price fluctuations and losses from some undisclosed events that are not included in statistics and other factors, the actual losses should be higher than the statistical results.
(https://hacked.slowmist.io/statistics/?c=all&d =2024)
Typical attack events(Security attack events that lost the Top 10 in 2024)
p>DMM BitcoinOn May 31, 2024, Japanese cryptocurrency exchange DMM Bitcoin stated that 4,502.9 BTC in its official wallet was illegally transferred, causing losses worth approximately 48.2 billion yen. It is reported that the amount of damage caused by the DMM Bitcoin security incident ranks seventh in the history of cryptocurrency hacking attacks and is the largest attack since December 2022. sameAt that time, there had been two major cryptocurrency exchange hacking incidents in Japan, namely the Mt. Gox incident in 2014 and the Coincheck incident in 2018, with the stolen amounts of US$450 million and US$534 million respectively. The DMM Bitcoin attack became the third largest such case in Japan. On December 23, according to a report from the FBI, the US Federal Bureau of Investigation (FBI), the Department of Defense Cybercrime Center (DC3), and the Japanese National Police Agency (NPA) reminded the public that the theft was related to the TraderTraitor threat activity. TraderTraitor is also tracked as Jade Sleet, UNC4899 and Slow Pisces. TraderTraitor campaigns often feature social engineering attacks targeting multiple employees at the same company.
It is reported that at the end of March 2024, a North Korean hacker disguised as a LinkedIn recruiter contacted employees of Ginco, an enterprise-level company headquartered in Japan. Cryptocurrency wallet software company. The hackers sent targeted employees a link to a malicious Python script hosted on GitHub, claiming it was an onboarding test. The targeted employee copied the Python code onto his or her own GitHub page and was compromised. After mid-May, TraderTraitor hackers used session cookie information to impersonate compromised employees and successfully accessed Ginco's unencrypted communications system. In late May, hackers may have used this access to tamper with legitimate transaction requests from DMM Bitcoin employees, resulting in the theft of 4,502.9 BTC. Eventually, the stolen funds were transferred to a wallet controlled by TraderTraitor.
PlayDappOn February 9, 2024, the blockchain gaming platform PlayDapp was attacked, and hackers invaded the PlayDapp (PLA) token smart contract. The hacker illegally obtained the private key, thereby changing the ownership and minting rights of the smart contract and transferring it to his own account. Hackers removed the authorization of existing administrators and illegally minted 200 million PLA tokens. Shortly after the incident, PlayDapp sent a message to the hacker through an on-chain transaction, demanding the return of the stolen funds and a $1 million white hat reward, but the negotiations ultimately failed. On February 12, hackers illegally minted 1.59 billion PLA tokens again, but because the exchange had taken freezing measures, market circulation had been stopped and could not be circulated. AprilOn the 1st, PlayDapp disclosed that on January 16, 2024, the PlayDapp team received a forged email from a hacker. The email was carefully designed and had exactly the same title and origin as the regular information request emails it often received from major partner exchanges. The sender's email address (including username and domain name) and content. Analysis shows that when the malicious code in the email attachment is executed, the victim's computer installs a tampered remote access multi-session tool, which is then remotely controlled by the hacker, leading to the theft of the administrator's private key.
WazirXOn July 18, 2024, the multi-signature wallet of the Indian cryptocurrency exchange WazirX was monitored for multiple suspicious transactions. On July 19, according to WazirX’s preliminary investigation results of the cyber attack released on the X platform, one of their multi-signature wallets suffered a cyber attack, resulting in a loss of more than $230 million. The wallet has a total of six signatories – five from WazirX team members and one from Liminal, responsible for transaction verification. Each transaction typically requires approval by three signatories from the WazirX team (all three signers use Ledger hardware wallets for security) before final approval by Liminal’s signer. The cyber attack originated from the discrepancy between the data displayed on the Liminal interface and the actual transaction content. At the time of the attack, the transaction information displayed on the Liminal interface did not match the actual signed content. WazirX suspects that the hacker transferred control of the wallet to himself by replacing the payload.
BtcTurkOn June 22, 2024, the Turkish cryptocurrency exchange BtcTurk was attacked, resulting in a loss of approximately US$90 million. BtcTurk said in a statement on June 22: "This cyber attack affected a portion of the balance of 10 cryptocurrencies in our hot wallets, and the majority of assets stored in cold wallets remain safe." According to Binance CEO Richard Teng It was revealed that Binance has frozen $5.3 million worth of the stolen assets.
MunchablesOn March 27, 2024, the Blast ecological project Munchables was attacked, causing a loss of approximately US$62.5 million. On the same day, Blast founder Pacman tweeted: "Blast core contributors have received $97 million in funding through multi-signature. Thank you to the former Munchables developer for choosing to eventually return all funds without requiringAsk for any ransom. ”
Radiant CapitalOn October 17, 2024, Radiant Capital issued a document on The online market has suspended trading. According to analysis by the SlowMist security team, this incident was caused by Radiant hackers illegally controlling three multi-signature permissions and upgrading the malicious contract to steal funds on October 18. The incident analysis report released stated that the incident resulted in a loss of approximately US$50 million. Hackers successfully invaded the devices of at least three core contributors through complex malware injection techniques. These compromised devices were subsequently used to sign malicious Transaction. On December 6, Radiant released the latest development of the attack. The security company Mandiant hired by Radiant attributed the attack to UNC4736, commonly known as AppleJeus or Citrine Sleet. UNC4736 is related to the Democratic People's Republic of Korea (DPRK)
BingXOn September 20, 2024, according to the announcement of the cryptocurrency exchange BingX, Singapore time on September 20. At around 4 a.m. on the same day, BingX’s security system detected an unauthorized intrusion into a hot wallet. According to statistics from the SlowMist security team, the incident resulted in losses of approximately US$45 million. According to MistTrack's analysis, there is a suspected connection between the Indodax hacker and the BingX hacker. The hackers in the two attacks used the same address to launder money, and both pointed to the North Korean hacker Lazarus Group
Hedgey FinanceOn April 19, 2024, Hedgey Finance was attacked. The hackers conducted a series of malicious transactions, resulting in a total loss of approximately approximately 100,000 USD on the Ethereum and Arbitrum chains. $44.7 million. The root cause of this incident was a lack of validation of user parameter inputs, which allowed hackers to manipulate and obtain unauthorized token approvals.
PenpieOn September 4, 2024, the decentralized liquidity income project Penpie was attacked, and the hackers made approximately US$27.35 million. According to the analysis of the SlowMist security team, the core of this incidentThe heartbreak is that Penpie mistakenly assumes that all markets created by Pendle Finance are legitimate when registering new Pendle markets. However, Pendle Finance’s market creation process is open, allowing anyone to create a market, and key parameters, such as the SY contract address, can be customized by users. Taking advantage of this, the hacker created a market contract containing a malicious SY contract, and used the mechanism that the Penpie pool needs to call the external SY contract when obtaining rewards, and used flash loans to add a large amount of liquidity to the market and pool, artificially amplifying the Reward amount and thus profit.
FixedFloatOn February 16, 2024, according to on-chain data, the cryptocurrency trading platform FixedFloat was attacked, resulting in a loss of approximately 409 BTC (approximately US$21.17 million) and 1,728 ETH (approximately $4.85 million). FixedFloat stated in response to this attack: This hacker attack was an external attack caused by a vulnerability in the security structure. It was not carried out by employees, and user funds were not affected. On April 2, FixedFloat stated on the X platform that it had once again been attacked by the same hackers as the February 16 attack. Hackers managed to exploit a vulnerability in a third-party service used by FixedFloat. The two attacks cost FixedFloat a total of approximately $29 million.
Rug PullRug Pull is a scam. Its essence is that malicious project parties create momentum to attract users to invest. When the time is right, they "pull the blanket" and run away with the money. . According to statistics from SlowMist Hacked, there were 58 Rug Pull incidents in 2024, resulting in losses of approximately US$106 million.
(2024 loss of Top 10 escape incident)
With the arrival of the Meme coin craze, many users have ignored potential risks, driven by speculation and FOMO emotions. Some currency issuers do not even need to describe their vision or provide a white paper to users. With just a concept or slogan, they can create buzz and attract users to buy tokens. The low cost of doing evil has led to endless incidents of escapes. The following are common operations performed by malicious project parties:
False publicity and momentum building: attracting user investment by exaggerating technical strength or market potential, as well as false cooperation or celebrity endorsement.
Manipulation of proxy Coin price: Project parties usually hold a large number of tokens in advance to create the illusion of prosperity by manipulating market prices to attract more funds.
Token contract setting vulnerability: By reserving a backdoor in the smart contract, the project party can withdraw funds or destroy the liquidity pool at any time.
Evaporated: On the eve of running away, project parties often close official websites, social accounts or dissolve communities to cut off contact with investors.
After understanding the operating methods of malicious project parties, we can find , these scams often take advantage of users’ speculative psychology and desire for high returns. To avoid becoming a victim of such scams, the key is to remain vigilant and enhance prevention and verification capabilities. The following methods can help users avoid participating in meetings as much as possible. Runaway projects:Review the project background: Pay attention to the authenticity and background of the team members, and check whether their past projects have bad records.
Whether it has been audited: Check whether the project has been audited After professional security audit.
Pay attention to community feedback: Join the project's social media or forum, observe the community activity and discussion content, and be wary of excessive praise or discussion. Unreasonable promises.
diversify investment: do not invest all your funds in one project to avoid major losses due to a single project.
Be wary of the temptation of high returns: nothing will fall from the sky High returns often come with high risks, so you need to be extremely cautious about unrealistic promises such as "quick doubling" and "zero risk".
Full report. The link is as follows, you can also click directly to read the original text and jump to it. Welcome to read and share:)
Chinese: https://www.slowmist.com/report/2024-Blockchain-Security-and-AML-Annual-Report(CN).pdf
English: https://www.slowmist.com/report/2024-Blockchain-Security-and-AML-Annual-Report(EN).pdf











