Source: Chainalysis; Compiled by: White Water, Golden Finance
In 2024, the cryptocurrency ecosystem has achieved many positive developments. Cryptocurrencies continue to gain mainstream acceptance on many fronts following the U.S. approval of spot Bitcoin and Ethereum exchange-traded products (ETPs) and revisions to the U.S. Financial Accounting Standards Board (FASB) fair accounting rules. Additionally, year-to-date inflows into legal services are the highest since 2021, the peak of the last bull market. In fact, total illegal activity is down 19.6% year-to-date, from $20.9B to $16.7B, indicating that legal activity is growing faster than on-chain illegal activity. This is an encouraging sign for the continued adoption of cryptocurrencies across the globe.
These global trends are also reflected in Japan’s crypto ecosystem. Overall, Japanese services generally have low exposure to global illicit entities, such as sanctioned entities, darknet markets (DNMs), and ransomware services, as most Japanese services are primarily targeted at Japanese users. However, this does not mean that Japan is completely immune to cryptocurrency-related crime. Public reports, including those from Japan’s Financial Intelligence Unit (FIU) Japan Financial Intelligence Center (JAFIC), have highlighted that cryptocurrencies pose significant money laundering risks. While Japan's engagement with internationally illegal entities may be limited, the country is not without its own local challenges. Off-chain criminal entities exploiting cryptocurrencies are common.
In this article, we will explore two key cryptocurrency crime issues in Japan that deserve close attention: money laundering and fraud.
Money Laundering and CryptocurrenciesFirst, let’s explore the relationship between money laundering and cryptocurrencies. Money laundering in the cryptocurrency context is often associated with concealing proceeds from on-chain crimes such as DNM and ransomware. But as the world continues to embrace cryptocurrencies, illicit actors are eager to take advantage of the powerful new technology. With the right tools and knowledge, investigators can leverage blockchain’s transparency to uncover and disrupt illegal activity on and off-chain.
Cryptocurrency Native Money LaunderingThe process of laundering funds obtained on-chain is often complex, as cybercriminals use a variety of services to mask the source and movement of the funds. Cryptocurrency-native money laundering poses ongoing challenges to cryptocurrency services and law enforcement agencies.
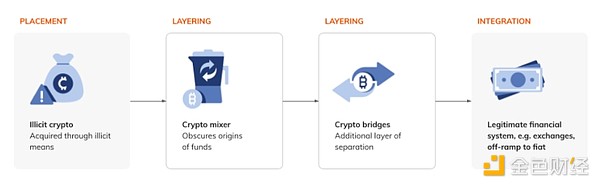
The first stage of cryptocurrency-native money laundering—placement—always involves cryptocurrency. Despite the transparency of blockchain, criminals often choose cryptocurrencies for money laundering because it is often easier to create private wallets that do not require know-your-customer (KYC) information than to launder money through traditional placement strategies as money mules. The intermediate stages of money laundering (stratification) can take many forms. In traditional fiat money laundering, this might involve sending funds through multiple bank accounts and/or shell companies. In cryptocurrencies, this may involve:
Intermediate wallets or hopping: using multiple personal wallets makes tracking complexcomplex, often accounting for more than 80% of the total value flowing through these money laundering channels. For investigators and compliance professionals using Chainalysis, detecting illegal activity and tracing it through intermediary wallets can be relatively simple.
Crypto obfuscation services: Obfuscation services can take many different forms, such as mixers, cross-chain bridges, and privacy coins. While these services are widely used by money launderers, they also have legitimate privacy use cases but are not inherently illegal.
Mixers: These services mix cryptocurrencies from different users to obfuscate the origin and ownership of the funds. In line with a general uptick in market activity, mixers will begin to recover in 2024.
Cross-chain bridges: These services and protocols facilitate the transfer of assets between different blockchain networks, creating complex transaction networks.
Privacy Coins: Coins like Monero and Zcash use advanced encryption to hide transaction details, which makes them attractive to illicit actors.
Stablecoins: Increasingly becoming the vehicle of choice for illicit money transfers, reflecting the overall growth in global stablecoin adoption over the past few years. But using stablecoins also increases the risk for money launderers, as many stablecoin issuers are responsive to authorities and have the ability to freeze funds.
Over-the-Counter (OTC) Brokers: OTC brokers are located around the world and can facilitate large transactions with minimal scrutiny, often bypassing public order books and KYC requirements.
While some cybercriminals may keep their ill-gotten gains in personal wallets for years (presumably in the hope that authorities will turn their attention elsewhere), most bad actors want to remove funds from crypto Currency is converted into cash. After using obfuscation technology, more than 50% of illicit funds flow directly or indirectly into centralized exchanges. Illicit actors may turn to centralized exchanges for money laundering because their high liquidity, easy cryptocurrency-to-fiat conversion, and integration with traditional financial services help blend illicit funds with legitimate activities. Hundreds of centralized services currently receive more than $1 million in illicit funds each year.
Non-Crypto Native Money LaunderingTraditional money launderers are using methods similar to fiat-based strategies to get into cryptocurrencies. Unlike cryptocurrency-native money laundering, non-cryptocurrency-native money laundering begins with the placement phase involving fiat currencies. Typically, criminals first use bank accounts to deposit fiat funds and then convert them into cryptocurrencies. Criminals can then layer their funds, much like crypto-native money laundering.
Non-cryptocurrency-native money laundering involves off-chain criminal activity, such as drug trafficking and fraud. Identifying novel on-chain money laundering patterns often reflects the detection of anomalous fiat-based transactions and patterns. In non-crypto-native money laundering, on-chain analysis often starts at centralized exchanges, making it difficult to identify illicit transactions without additional context. exhaustWhile tracking the movement of these funds can be challenging due to a lack of evidence, data science techniques can flag indicators of potential non-cryptocurrency-native money laundering.
One way to identify non-cryptocurrency native money laundering is repeated transfers below reporting thresholds, which we discuss in more detail in our 2024 Cryptocurrency Money Laundering Report. While these thresholds vary by /region, the Financial Action Task Force (FATF) – the international body that sets AML/CFT standards – recommends that cryptocurrency transactions above $1,000/€ should be subject to the travel rules. Authorities set that threshold at $3,000. Additionally, the U.S. Bank Secrecy Act (BSA) requires reporting of cash transactions over $10,000.
Transactions above these values trigger additional scrutiny, while transactions below these thresholds, even for just one dollar, do not face the same level of scrutiny.
The chart below shows the value of funds transferred to centralized exchanges by transfer size year-to-date in 2024. It showed a significant surge in transfer amounts, just below and slightly above the reporting thresholds of $1,000, $3,000 and $10,000. Transfers slightly above these thresholds may be due to rounding differences in exchange rates. This surge is typical of bad actors adjusting payment methods to avoid triggering reporting requirements. Transactions that fall slightly below reporting requirements are one of the red flag indicators highlighted by the FATF in its guidance for virtual asset service providers (VASPs) to help identify suspicious behavior.
Integrated FundsExchanges may also benefit from consolidated wallets that monitor interactions with their services. When money launderers layer funds through many intermediary wallets, the transaction flow is often not simple and linear. Instead, a money launderer may split the funds into many different wallets and then reconsolidate the funds after multiple transactions.
Merge wallets receive and merge funds from multiple wallets or sources. If funds are moved through multiple independent intermediary wallets and then consolidated at a single address, this may indicate an attempt to avoid detection.
The Chainalysis Cryptocurrency Investigation chart below illustrates this type of behavior among a known fraud ring targeting the elderly. In this case, the scammer may instruct the victim to purchase cryptoassets using a specific service, Exchange 1. Each victim is then instructed to send funds to a different wallet controlled by the scammer. The scammers then consolidated the funds into a wallet and cashed them out at Exchange 2.
Exchange 1’s compliance team would have a difficult time directly linking victims to scammers, especially if the intermediary address was a one-off and had no prior illicit relationship unless they Trace transactions back to the merged wallet. Using many intermediaries prior to integration is a well-known tactic to preventExchange 1's compliance team understands the connections between all victims who sent funds.
While the above example is relatively simple, more complex money laundering networks have integrated wallet capabilities that can aggregate funds from dozens or even hundreds of intermediary wallets. Querying Chainalysis data can allow investigators to find major integrated wallets, which often serve as useful clues. For example, the top 100 Bitcoin integrated wallets year-to-date in 2024 - all of which have two-hop transactions from exchanges - have received nearly $1 billion ($968 million) worth of Bitcoin from more than 14,970 different addresses currency.
Broadening the scope further, we found that over 1,500 combined wallets received a total of $2.6B worth of Bitcoin in 2024; each of them received from at least ten different wallets to funds. Again, we can't say with certainty that this represents money laundering - in fact, much of it likely represents legitimate inflows. But this activity may require additional scrutiny.
Illegal Activities in Japan: Money Laundering and ScamsIn Japan, based on our conversations with key industry players and statistics and documents published by local authorities, we have consistently observed that the most common illicit uses of cryptocurrencies are Money laundering from non-crypto native crime and scams. We discuss how Japan recognizes these issues and explore how to estimate the extent of damage caused by such crimes.
Money Laundering for Non-Cryptocurrency CrimeAs mentioned previously, non-crypto-native crime cases are difficult to trace at scale without context – often only law enforcement, financial institutions, crypto services and/or victims The person knows. Nonetheless, some of our clients have provided us with information that addresses attribution issues, allowing us to better understand the landscape of non-cryptocurrency money laundering in Japan. Based on the information we have received to date, many of the illicit accounts on centralized exchanges are used to steal funds from online banking accounts in order to receive fiat funds from traditional forms of fraudulent activity and phishing campaigns. We published a blog last year discussing on-chain analysis of a Japanese money laundering case that began with a non-cryptocurrency-native crime.
According to 2023 statistics released by the Japan National Police Agency (JNPA), in 2023, a total of 19,038 fraud cases were reported in Japan, with total losses reaching 45.26B yen (approximately US$300 million). These figures exceed those for 2022, indicating that this type of fraudulent activity is still growing and remains a serious problem. Although these statistics do not address the amount of fiat currency converted to cryptocurrencies, as we explore later, we assess that a large portion of this is cryptocurrency-based money laundering activity.
Nearly half of the funds reported stolen from online bank accounts in this case, totaling 8.73B yen (578$90,000)) was sent to the cryptocurrency exchange’s bank account. These fund flows indicate that cryptocurrencies are now being used as a common tool for fraudsters to launder money.
Scam Trends Impacting JapanAs our Cryptocurrency Crime Report explains, scams are one of the most serious illegal categories in cryptocurrency. We’ve previously uncovered prominent clusters of cryptocurrency scams with touchpoints in Japan, but today, Japanese law enforcement agencies are also keeping a close eye on new trends in scams – social media-based investment scams and romance scams.
Recent investment scams often run ads soliciting investments on major social media platforms to attract the attention of potential victims. Scammers impersonate well-known economists or celebrities to attract more followers and direct them to group channels on popular messaging apps through URLs on ads, where many fake members actively comment and applaud the channel moderators. Victims are drawn into conversations with scammers (who often claim to be channel owners or assistants) and are eventually directed to trade on fake investment websites.
Romance scams, also known as “pig-killing scams” because bad actors say they “fatten” their victims to obtain the greatest possible value, are a significant and growing problem with cryptocurrencies problem. The scammer first develops a relationship (usually romantic, as the name suggests) with the victim for a period of time, often initiating contact by pretending to send a text message to the wrong number or via a dating app. As the relationship deepens, the scammer will eventually prompt the victim to invest funds (sometimes in cryptocurrency, sometimes in fiat currency) into a fake investment opportunity and continue to do so until the connection is eventually severed.
JNPA’s latest statistics on this type of fraud show that the numbers from January to August this year are as follows, significantly higher than last year:
Investment fraud: 6,868 cases reported, totaling 64.14 billion yen ($424.97 million) - 9.9% of which is cryptocurrency
Romance scams: 4,639 cases reported, totaling 236.5 billion yen ($156.7 million) - 17.7% of which are cryptocurrencies
After Japan recognized this as a major threat to Japanese citizens, the cabinet held a meeting to discuss countermeasures and, including strengthening investigations into cryptocurrencies capabilities, prevent illegal bank withdrawals and establish a legal framework to fully support asset seizure and recovery.
Our on-chain analysis of fraud and scam cases in JapanWhile tracking off-chain money laundering activity at scale is difficult, when our clients alert us to this activity and provide the addresses and transactions involved, we Money flows can be tracked, just like we did last year. As we continue to work closely with clients and partners in Japan to enhance our data, particularly on off-chain money laundering activity, we can also analyze the landscape of fraud and scams involving cryptocurrencies in Japan.
The following are 2023 and 202Total receipt value of clusters of accounts and scams reported as fraudulent over 4 years (to June).
Reported as Fraud (Non-Crypto Native) (Total Value Received from Japanese Exchanges) – USD
< p style="text-align: center;">Reported as Scam (Total Value Received from Japanese Exchanges) - USDAs always, we must remind Note that these numbers are lower estimates, especially for off-chain crime, as many scams and frauds go unreported.
Nevertheless, these activities all have a common pattern: the use of integrated wallets. Although the initial addresses that receive funds directly from the exchange are distributed and ephemeral, funds from these addresses are eventually sent to a much smaller number of private wallets and/or deposit addresses on the exchange.
When we narrowed down the cases involving ETH, we found that integrated wallets often use decentralized exchanges (DEX) or bridges to exchange ETH for USDT.
How to read this graph:
– Blue: funds flowing from Japanese exchanges to suspected scam addresses
– Red: funds From the initial address to the first consolidation point
– Green: Funds from the first consolidation point to the second consolidation point
– Purple: Funds to DEX from second integration point (ETH<->USDT)
Given how quickly money launderers use new wallet addresses, it’s not easy to track them individually in real time, but we still Common integration points can be identified from the clusters we have identified to estimate the scale of these illegal activities. In this case, we followed the following process to estimate the amount of potential illicit funds associated with the Japanese case:
Trace funds that have been classified as illicit clusters in Japan to find points of consolidation;
< p>At the merge point, the received exposure amounts from the Japan Tags cluster and the Japan Exchange cluster are aggregated.Here’s what we found:
Estimated value of non-crypto-native money laundering activity – USD
p>
Estimated value of Japan scam – US dollars
As stated previously, these estimates are consistent with those published by Japanese authorities .
The changes in money laundering tactics we are seeing from numerous threat actors are a reminder that the most sophisticated illicit actors are constantly adapting their money laundering strategies and leveraging new crypto services. By studying these new on-chain money laundering methods and models and learning how to disrupt them, law enforcement and compliance teams canto be more effective.












