Author: M31 Capital Portfolio Manager David Attermann, CoinDesk; Compiled by: Whitewater, Golden Finance
Centralized data networks (networks owned or managed by a single entity) have been structurally broken for years . Why? Single point of failure. If one entity (or even several entities) has access to the database, there is only one "point" of compromise required to gain full access. This is a serious problem for networks that hold sensitive data such as customer information, documents and financial records, as well as those that control infrastructure such as power grids.
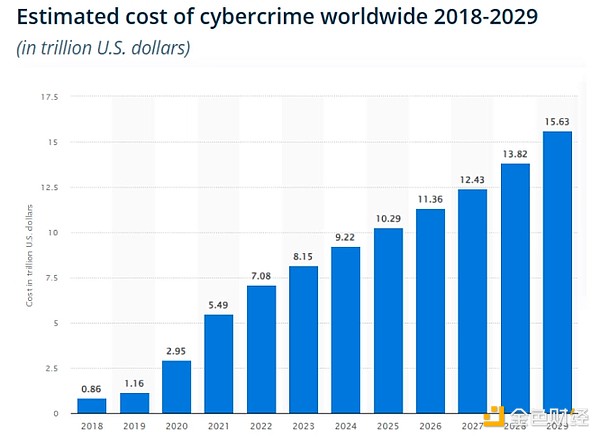
Billions of digital records will be stolen in 2024 alone, causing an estimated $10 trillion in losses! Notable breaches include nearly all of AT&T's customer information and call records, half of all U.S. personal health information, 700 million end-user records from companies using Snowflake, 10 billion unique passwords stored on RockYou24, and 300 million Americans' social Safeguarding records.
This is not just a private sector problem - and critical infrastructure also relies on centralized networks. Recent notable breaches include the theft of 22 million Americans’ records from the U.S. Office of Personnel Management, sensitive communications from multiple U.S. federal agencies, and more.
Despite hundreds of billions of dollars being spent on cybersecurity every year, data breaches are growing in size and occurring with increasing frequency. It was clear that incremental products could not fix these network vulnerabilities—the infrastructure had to be completely re-architected.
AI magnifies the problemRecent advances in generative AI are making it easier to automate routine tasks and increase productivity. But the most useful and valuable AI applications require context, namely access to sensitive user health, financial and personal information. Since these AI models also require significant computing power, they essentially cannot be run on consumer devices (computers, mobile devices) and must instead access public cloud networks such as AWS to handle more complex inference requests. Given the severe limitations inherent in centralized networks described earlier, the inability to securely connect sensitive user data to cloud AI has become a significant barrier to adoption.
Even Apple made this point in its Apple Intelligence announcement earlier this year, noting the need to be able to get help from larger, more complex models in the cloud, and how traditional cloud models No longer feasible.
They cited three specific reasons:
Privacy and security verification: Provider claims (such as not logging user data) often lack transparency and enforcement. Service updates or infrastructure troubleshooting can inadvertently log sensitive data.
Lack of runtime transparency: Providers rarely disclose software details, even when using open sourceTools, users also cannot verify that the service is running without modification or detect changes.
Single point of failure: Administrators require advanced access to perform maintenance, thereby risking data being accidentally leaked or misused by attackers targeting these privileged interfaces.
Fortunately, the Web3 cloud platform provides the perfect solution.
Blockchain Orchestrated Confidentiality Cloud (BOCC)The BOCC network is similar to AWS, except it is built entirely on confidential hardware and is managed by smart contracts. While still in its early stages, the infrastructure has been in development for several years and is finally starting to support Web3 projects and Web2 enterprise customers.
This technology addresses all of Apple’s previously mentioned concerns:
Privacy and security verification: Through a public smart contract orchestration network, users can verify that user data is transferred and used as promised .
Workload and program transparency: The network also verifies the work done in the confidential TEE, cryptographically proving that the correct hardware, data, and software were used and that the output has not been tampered with. This information is also submitted on-chain for everyone to review.
Single point of failure: Network resources (data, software, hardware) can only be accessed through the owner’s private key. Therefore, even if one user is compromised, only that user's resources are at risk.
While cloud AI brings huge disruption opportunities to Web3, BOCC can be applied to any type of centralized data network (power grid, digital voting infrastructure, military IT, etc.) without sacrificing performance. Provide superior and verifiable privacy and security or latency. Our digital infrastructure has never been more fragile, but blockchain orchestration can fix it.












