Author: Guy Wuollet, partner at a16z Crypto; Translation: Golden Finance xiaozou
Existing physical infrastructure networks such as telecommunications, energy, water supply and transportation are often natural monopoly markets—the cost of services provided by a single enterprise is much lower than in a competitive environment. In most developed countries, these networks are subject to complex regulatory and regulatory constraints, resulting in a lack of innovation momentum, not to mention poor customer experience, backward user interface, mediocre service quality and slow response speed. These inefficient and poorly maintained conditions are by no means a coincidence, as evidenced by the California wildfires that led to PG&E bankruptcy or the protective regulations of traditional telecom companies. In the developer, the situation is even more serious: these basic services are either missing or expensive and scarce.
We can do better. The decentralization of physical infrastructure networks provides us with opportunities for leapfrog development, and can bypass the rigid traditional monopoly system and establish a stronger, easier to invest and more transparent network. The essence of the DePIN protocol is a service system owned and operated by users, allowing anyone to participate in maintaining the construction of critical infrastructure in daily life. It is expected to become a powerful democratization force and promote society to develop in a more efficient and open direction.
This article will explain the definition and value of DePIN, and share the framework system for evaluating the DePIN protocol, focusing on the core issue that needs to be paid attention to when building the DePIN protocol - the verification mechanism.
1. What is DePIN?Decentralized Physical Infrastructure Network (DePIN) refers to a fully decentralized network that uses cryptography and mechanism design to ensure that customers can obtain physical services from the service provider group, which can break the natural monopoly pattern and release competitive dividends (the article will be expanded in detail later). Customers are usually end users, and may also be applications representing users; most of the providers are small and medium-sized enterprises, and may also cover gig workers and even industry giants. "Decentralization" here emphasizes the dispersion of power and control, rather than just the decentralization of physical distribution or data structures.
The properly designed DePIN protocol can inspire users and small and medium-sized enterprises to participate in physical infrastructure networks, and jointly participate in network governance while contributing transparency. Just as the Internet is dominated by user-generated content, DePIN makes it possible for user-generated services to dominate the physical world. More importantly, just as blockchain is breaking the "attraction-extraction" of tech giantsMonopoly cycle, the DePIN protocol is expected to disintegrate real-world utility monopoly.
2. DePIN practice case: power grid systemTake the energy field as an example. The U.S. power grid system is spontaneously moving towards decentralization, and this trend is even ahead of the intervention of encryption technology. The delay in connecting the transmission bottleneck and new power generation facilities to the grid have given birth to a business model of distributed power generation. Homes and businesses can realize power generation at the edge of the grid by installing solar panels, or configure energy storage batteries to regulate power supply. This means that they can not only buy electricity from the power grid, but also sell electricity in the reverse direction.
With the popularity of distributed power generation and energy storage, a large number of power grid connection equipment is no longer controlled by utilities. These users' own equipment could have optimized grid operation through charging and discharging during critical periods, but why did it not be realized? The existing utility system lacks effective means to obtain user equipment status data or purchase its control rights. The energy industry agreement Daylight proposes a solution: build a decentralized network so that users can sell equipment status data, and energy companies can pay for temporary control - in short, Daylight is building a decentralized virtual power plant.
Compared with the centralized monopoly model, this model is expected to create a more reliable and efficient power grid system, realizing user-owned power generation, improving data quality and simplifying trust assumptions. This is exactly what DePIN promises.
3. DePIN construction guideDePIN protocol has great potential to innovate daily physical infrastructure, but achieving this vision requires three major challenges:
· Determine whether specific scenarios really require decentralization
· Market-oriented strategy formulation
· Verification mechanism design (the most severe challenge)
>This article intends to avoid technical difficulties in specific physical infrastructure fields—not because it is not important, but because it is highly professional. We will focus on the abstract construction principle of decentralized networks and provide universal advice for cross-industry DePIN projects.
(1) Why choose DePIN?
The two common causes of building the DePIN protocol are reducing capital expenditures (capex) for hardware deployment and integrating fragmented production capacity. In addition, DePIN can be built based on physical infrastructureA neutral developer platform that enables permissionless innovation through open APIs (such as energy data interfaces) or neutral sharing markets. Through decentralization, the DePIN protocol enables censorship resistance, eliminates platform risks, and activates permissionless innovation—this composability and permissionless innovation are the key to the success of Ethereum and Solana. The construction of traditional physical infrastructure networks relies on centralized enterprises and is expensive, while DePIN realizes a distributed configuration of cost and control through ownership decentralization.
Capex Advantages
Many DePIN protocols encourage users to participate in network operations by purchasing hardware, which avoids centralized enterprises from bearing huge capital expenditures. Capital expenditure is exactly one of the main reasons for most infrastructure being regarded as natural monopoly, and lower capital expenditure gives DePIN structural advantages.
Taking the telecommunications industry as an example: the promotion of new network standards is often hindered by the high-value capex deployment of supporting hardware. Some analysts predict that the deployment of 5G networks in the United States will require US$275 billion in private investment. In contrast, the DePIN project Helium has built the world's largest long-distance low-power (LoRaWAN) network without a single entity's large initial investment. LoRaWAN is a very suitable standard for Internet of Things (IoT) use cases. Helium cooperates with hardware manufacturers to launch LoRaWAN routers, where users purchase equipment directly from manufacturers to become network operators, providing data transmission services to paying customers. Helium is currently expanding 5G cellular network coverage.
If you use the traditional model to deploy the Internet of Things network of the same scale, it not only requires huge initial investment, but also bear the risk of insufficient user base. As the DePIN protocol, Helium successfully verified the market supply side and optimized the cost structure.
Capacity aggregation effect
Some physical resources have a large amount of idle production capacity, but traditional enterprises are difficult to effectively integrate. Take the idle space of a hard disk as an example: the idle space of a single hard disk is insignificant to cloud storage providers such as AWS, but after aggregation through DePIN protocols such as Filecoin, these fragmented spaces can form cloud storage services. The DePIN protocol uses blockchain technology to coordinate ordinary individuals so that they can contribute to large networks.
Unlicensed Innovation
The most critical feature of the DePIN protocol is the support of licenseless innovation - anyone can build at the protocol layer, which is in sharp contrast to the power grid of local power companies. The value of this feature is often underestimated compared to reducing capex or aggregate capacity.
Privacyless innovation enables physical infrastructure to evolve at the speed of software iteration. People often praise the innovation speed of the "bit world", but they lament the innovation hysteresis of the "atom world". For builders and investors, DePIN provides the best path to bridge the gap between the two worlds. When any internet user around the world can propose new ways of organizing physical systems, intelligence and creativity will give birth to solutions that exceed existing levels.
Composibility
The root cause of permissionless innovation to accelerate the evolution of "atoms" lies in composability. It allows builders to focus on developing the best single point solutions and enable easy integration. The "Lego of Currency" in the DeFi field has shown this power, and DePIN's "Lego of Infrastructure" will have the same impact.
(2) Marketization: Opportunities and Challenges
Building a DePIN protocol is more complex than developing a blockchain, because it requires solving the dual challenges of decentralized protocols and traditional business at the same time. Both Bitcoin and Ethereum were initially independent of traditional finance and cloud computing systems, and most DePIN protocols had to face the existing problems of the physical world.
Most DePIN fields need to interact with centralized systems from the beginning (such as utilities, cable TV, online ride-hailing and ISP). These existing networks often enjoy regulatory constraints and strong network effects protection, making it difficult for new entrants to compete. Just as decentralized networks are the natural antidote to Internet monopoly, DePIN networks can become the nemesis of physical infrastructure monopoly.
DePIN builders need to find the right value entry point first, and then gradually expand to challenge the entire physical network. Finding this "wedge" is crucial to future success. At the same time, it is necessary to clarify the interface between the network and existing alternatives - traditional enterprises usually have technical obstacles to running full nodes, autonomous hosting, or on-chain transactions, and generally lack encryption awareness.
Effective policyThe following is: first prove the value of the protocol (not mentioning the underlying encryption layer for the time being), and then introduce the concept of encryption after the partner recognizes the value. In short, builders should transform the agreement value proposition based on audience characteristics and build a narrative framework of emotional resonance.
From a tactical perspective, interfaces to existing networks usually require early intermediary services and fine physical structure design, which are highly relevant to the target area.
Enterprise-level sales are another major challenge. This type of sales usually requires customized, high-contact service processes, and customers require clear responsible parties. However, the DePIN network does not have a single representative entity, and the traditional sales model is difficult to apply. The solution is to introduce centralized enterprises as early stage distribution partners. For example, a centralized mobile phone company sells directly to ordinary consumers and charges US dollars while using a decentralized telecommunications network to actually provide services. This abstracts the complexity of crypto wallets and self-hosted wallets and hides the “encryption” nature of the product.
(3) The biggest problem of DePIN: verification mechanism
Verification is the most difficult part of building a DePIN protocol, and it is also the only reliable way to ensure that customers receive paid services and providers receive the correct reward.
Pool-to-pool mode vs point-to-point mode
Most DePIN projects adopt the "customer-fund pool-service pool" mode: the customer initiates a request to the network and the network allocates the service provider to respond. This means that customers pay the Internet and then settle the Internet with the service provider.
The alternative is a peer-to-peer model: the customer directly requests service from the service provider. This requires customers to discover available service providers and make independent choices, and payments are also completed directly.
Pools have higher requirements for pool mode for verification. In the peer-to-peer mode, although there is a possibility of fraud, due to direct payment, any party can terminate the transaction if it discovers fraud without proofing to the network. In the pool-to-pool model, the network needs an arbitration mechanism to resolve disputes - service providers usually promise to obey network allocation as an access condition, so the prevention or resolution of disputes can only rely on decentralized verification.
DePIN project selection pool has two major reasons for pool design: one is to facilitate the issuance of subsidies through native tokens; the other is to optimize the user experience and reduce off-chain infrastructure dependence (such as Uniswap and 0the difference between x).
Tokens can solve the problem of cold startup of the network. In order to establish a network effect (both Web2 and Web3), the project party usually needs to provide subsidies (including direct economic incentives or value-added services). Tokens can provide economic subsidies, cultivate communities and give customers the right to govern.
Pool-to-pool mode allows customers to pay X and the service provider obtains Y (XY, and the protocol obtains the difference in profits.
Ping-to-peer model is difficult to implement token subsidies. If the customer pays X, the service provider obtains Y (X
Self-trading issues
When a user plays the role of a customer and a service provider at the same time and obtains network value through self-transaction, it constitutes self-transaction. The easiest solution to self-trading is to cancel the token incentive, but this will increase the difficulty of cold start.
When the self-transaction service cost is zero (usually so), the harm is especially serious. A common solution is to require service providers to pledge tokens (usually native tokens) and assign customer requests by pledge weight.
Staking does not completely solve the problem - large pledgers may still make money by requests allocated to themselves. For example, when the service reward is 5 times the customer's cost, a service provider holding a 25% pledge can receive 5 rewards for every 4 tokens spent (assuming that the self-transaction service cost is zero and the benefit from other requests is zero). If the trader can benefit from other allocation requests, there is greater arbitrage space.
Verification mechanism
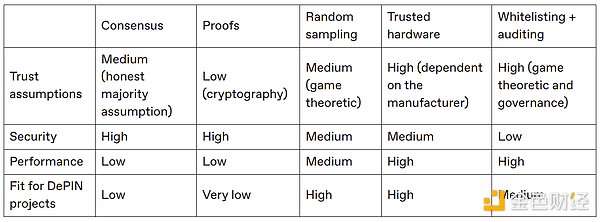
Since we have understood why verification is such a critical issue, let's discuss what verification mechanisms can be considered in DePIN projects.
Consensus mechanism
Most blockchains adopt consensus mechanism (combined with anti-witch attack solutions such as PoW/PoS). It is more accurate to understand "consensus" as "re-execution" - each node in the network usually needs to re-execute all calculations (modular blockchains may be exceptions). This design originates from the prevention of Byzantine behavior, and nodes must verify the results of each other. The cost of re-execution of more than 6,000 nodes on the entire Ethereum network is obvious.
Re-execution processes are usually transparent unless trusted execution environment (TEE) or fully homomorphic encryption is used.
Proof of correct execution (validity rollup, ZEXE, etc.)
Unlike requiring each node in a blockchain network to re-execute each state change, a single node can be allowed to perform a given state change and generate a proof of correct execution of the state change that node. Verifying the proof that is correctly executed is faster than performing the calculation itself (this property makes the proof concise). The most common form of this proof is SNARK (concise non-interactive knowledge argument) or STARK (concise and transparent knowledge argument). SNARK and STARK are usually extended to zero-knowledge proofs, not revealing any information about proven statements. Therefore, when used to compress the proof of calculation, you often see SNARK/STARK and ZK proof appear together.
The most famous blockchain type that uses the correct execution of proof is probably ZK rollup (ZKR). A ZKR is an L2 blockchain that inherits part of the security of the underlying blockchain. ZKR batches the transaction, creates a proof that the transaction is executed correctly, and then publishes the proof on L1 for verification.
Proof of correct execution is usually used for scalability and performance, privacy, or both. zkSync, Aztec, Aleo and Ironfish are all good examples. Proof execution of the proof can be used in other scenarios. Filecoin uses ZK-SNARK as part of its storage proof. Correct execution of proof has begun to be deployed in the fields of machine learning inference, machine learning training, identity recognition, etc.
Random sampling/statistical measurement
Verify the quality of service provider response through random sampling. "Challenge Requests" are usually assigned according to the pledge weight, which not only verifies service quality but also prevents self-transactions. Depend onOnline rewards are often higher than service rewards, and sampling can ensure that service providers are truly online. A challenge request will be randomly sent to a service provider. If the service provider responds to the request correctly and the hash value of the request exceeds a certain difficulty threshold, the service provider will receive a response reward (equivalent to a block reward). If the service provider cannot distinguish between client requests and challenge requests, it is a rational choice to respond correctly to client requests. Some versions of random sampling have been maximized in network-focused DePIN projects, such as Nym, Orchid, Helium.
Compared with the consensus mechanism, sampling verification is more scalable—the sample size can be much smaller than the number of state changes. Trusted hardware
Trusted hardware can be used to protect privacy (as mentioned above), but it can also be used to verify sensor data. One of the biggest challenges with decentralized validation for DePIN projects is that DePIN projects must be born with oracle issues (bring data from physical space to blockchain in a way that is trustless or minimizes trust). Trusted hardware allows the network to adjudicate any customer/provider disputes based on the results of physical space sensor data. Trusted hardware often has vulnerabilities, preferably as a practical solution in the short and medium term, or as another deep defense measure. The most common trusted execution environments are Intel SGX, Intel TDX, and ARM TrustZone. Chains such as Oasis, Secret Network and Phala all use trusted execution environments, and SAUVE plans to use trusted execution environments.
Whitelist and audit mechanism
The most pragmatic and least technically complex verification solution is often to access specific physical devices through the whitelist mechanism to participate in the DePIN protocol, and rely on manual auditors to review logs and telemetry data to ensure service providers operate in compliance. Specific implementation usually includes: customizing hardware devices equipped with embedded signature keys, requiring that all network access devices must be purchased from certified manufacturers. Manufacturers whitelist embedded key groups and the network only accepts data signed by whitelist key pairs. This solution needs to meet two prerequisites: the device key is extremely difficult to extract, and the manufacturer accurately records the correspondence between the key and the device. Manual audits are often used to solve potential problems in these links.
Ultimately, in order to ensure the quality of service, the DePIN protocol often passes a governance mechanism to electThe "auditor" detects malicious behavior and submits reports. Human auditors can identify complex attack patterns that are difficult to detect in standardized protocols—those attacks are often obvious once exposed to human perspectives. Auditors are usually authorized to submit punishment proposals (such as token confiscations) to the governance system, or to issue punishment incidents directly. This mechanism implies another premise: the protocol governance system can put protocol interests first, but it needs to deal with the human incentive problem in social consensus.
Optimal solution selection
In the face of diversified verification solutions, emerging DePIN protocols often face selection dilemma:
Consensus mechanisms and correctness proofs are often inapplicable - they can only ensure the verifiability of digital state changes, while DePIN involves physical service verification, and an additional oracle must be introduced (bringing the secondary trust assumption).
Random sampling has the advantages of high efficiency and game theory, and can well adapt to physical service verification scenarios. Trusted hardware and whitelisting mechanisms are the simplest and easy to implement, suitable for initial startup, but their centralized features may affect long-term sustainability.
4. Why is DePIN crucial?The rise of encryption technology originated from the vision of currency monopoly, but the monopoly of more basic services such as Internet access, electricity, and water supply has been controlled by a few groups for a long time. Through DePIN, we can not only build a more free society, but also create a more efficient and prosperous form of civilization.
The future of decentralization means that innovative solutions are no longer limited to a few elites, but instead activate human capital that is spread all over the world. If you are excited about decentralized finance or developer platforms, you might as well extend this beautiful vision to those more basic but also urgently needed network services in daily life.












