Author: Callum Reid, CoinTelegraph; Compiled by: Wuzhu, Golden Finance
Address poisoning attack is a malicious means used by attackers. Attackers can rerout traffic, interrupt services, or access sensitive data by inserting fake data or changing routing tables. These attacks exploit flaws in network protocols that seriously threaten the integrity of data and network security.
This article will explain what an address poisoning attack is, its type and consequences, and how to protect yourself from such attacks.
What is an address poisoning attack in cryptocurrency?In the cryptocurrency world, hostile behavior by attackers to influence or deceive consumers by tampering with cryptocurrency addresses is called address poisoning attacks.
On the blockchain network, these addresses composed of different alphanumeric strings are the source or destination of the transaction. These attacks use various methods to undermine the integrity and security of crypto wallets and transactions.
Address poisoning attacks in encrypted spaces are mainly used to illegally acquire digital assets or damage the smooth operation of blockchain networks. These attacks may include:
TheftThe attacker may use strategies such as phishing, transaction interception, or address manipulation to trick users into transferring funds to malicious addresses.
BreakAddress poisoning can damage the normal operation of the blockchain network by introducing congestion, delays or interrupts into transactions and smart contracts, thereby reducing the efficiency of the network.
SpoofingAttenders often try to mislead cryptocurrency users by impersonating famous people. This can undermine the community’s trust in the network and can lead to mistransactions or user confusion.
To protect the overall integrity of digital assets and blockchain technology, address poisoning attacks highlight the importance of strict security procedures and the ongoing attention within the cryptocurrency ecosystem.
Types of Address Poisoning AttacksAddress Poisoning Attacks in Encrypted include phishing, transaction interception, address reuse, witch attacks, fake QR codes, address spoofing, and smart contract vulnerabilities. Each attack poses a unique risk to user assets and network integrity.
Phing AttacksIn the cryptocurrency space, phishing attacks are a common type of address poisoning, where criminals create fake websites, emails, or communications that are very similar to well-known companies such as cryptocurrency exchanges or wallet providers.
These fraudulent platforms try to trick unsuspecting users into leaking their login information, private keys, or mnemonic words (recovery/seed phrases). For example, once this information is obtained, an attacker can conduct illegal transactions and unauthorized access to the victim's Bitcoin assets.
For example, a hacker might build a fake exchange website that is exactly the same as a real exchange website and asks consumers to log in. Once they do this, the attacker can get the client funds of the actual exchange, which will result in huge financial losses.
Transaction InterceptAnother way to address poisoning is transaction interception, where an attacker intercepts valid cryptocurrency transactions and changes the target address. By changing the recipient address to an attacker-controlled address, funds sent to the real recipient can be transferred. Such attacks usually involve malware damaging a user's device or network or both.
Address ReuseAttenders will monitor whether there are duplications in the blockchain, and then use this situation to benefit themselves. Reusing an address can endanger security because it can reveal the transaction history and vulnerabilities of the address. Malicious actors use these weaknesses to access user wallets and steal funds.
For example, if a user always gets funds from the same Ethereum address, an attacker may notice this pattern and exploit a vulnerability in the user's wallet software to access users' funds without authorization.
Sybil AttackIn order to exert disproportionate control over the operation of a cryptocurrency network, a Sybil attack requires the creation of multiple fake identities or nodes. Through this control, an attacker can modify data, deceive users, and may even endanger the security of the network.
Attenders may use a large number of fraudulent nodes in a Proof of Stake (PoS) blockchain network to significantly influence consensus mechanisms, allowing them to modify transactions and potentially make double payments to cryptocurrencies.
Forged QR code or payment addressAddress poisoning may also occur when a forged payment address or QR code is distributed. Attackers often send these fake codes in physical form to unwarranted users to trick them into sending cryptocurrencies to their unplanned locations.
For example, a hacker may spread a cryptocurrency wallet QR code that appears to be true but actually makes minor changes to the encoded address. Users who scan these codes will inadvertently send money to the attacker's address instead of the intended recipient's address, causing economic losses.
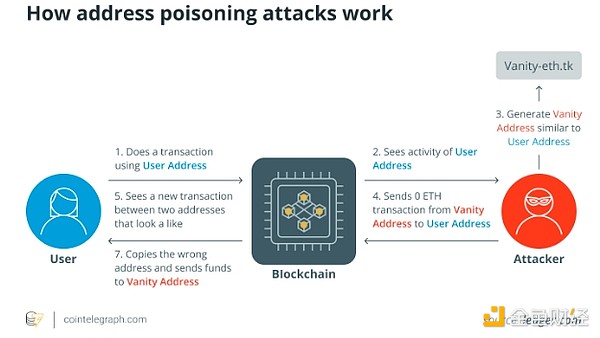
Address spoofingAttenders using address spoofing create cryptocurrency addresses that are very similar to the real address. The purpose is to trick users into transferring money to the attacker's address, not the address belonging to the intended recipient. This approach to address poisoning takes advantage of the visual similarity between fake and real addresses.
For example, an attacker might create a Bitcoin address that is very similar to the donation address of a well-known charity. Uninformed donors may inadvertently transfer the money to the attacker’s address when sending donations to the organization, thereby transferring the money from the intended use.
Smart Contract VulnerabilityAttenders use flaws or vulnerabilities in decentralized applications (DApps) on blockchain systems or smart contracts to poison addresses. An attacker can rerout funds or cause the contract to run unexpectedly by tampering with the execution of transactions. Users may suffer from capital losses as a result, and decentralized finance (DeFi) services may be interrupted.
Consequences of Address Poisoning AttacksAddress Poisoning Attacks can have a devastating impact on the stability of individual users and blockchain networks.Since attackers can steal cryptocurrency assets or change transactions to rerout funds to their wallets, these attacks often cause huge economic losses to victims.
In addition to money losses, these attacks may also lead to a decline in confidence among cryptocurrency users. If users get stuck in fraudulent plans or valuables are stolen, their trust in the security and reliability of blockchain networks and related services can be compromised.
In addition, some address poisoning attacks, such as Sybil attacks or the abuse of smart contract vulnerabilities, may prevent the blockchain network from functioning properly, resulting in delays, congestion, or unforeseen consequences that affect the entire ecosystem. These impacts underscore the need for strong security controls and user awareness in the crypto ecosystem to reduce the risk of address poisoning attacks.
How to Avoid Address Poisoning AttacksIn order to protect users' digital assets and ensure the security of blockchain network, it is crucial to avoid address poisoning attacks in the cryptocurrency world. The following methods may help prevent being targeted by such attacks:
Using a new addressUsing a new crypto wallet address for each transaction can reduce the likelihood of an attacker linking an address to someone’s identity or past transactions. For example, a hierarchical determinism (HD) wallet can be used to reduce address poisoning attacks that create new addresses for each transaction and reduce the predictability of addresses.
Using HD wallets can improve users' protection against address poisoning attacks, because automatic address rotation of wallets makes it more difficult for hackers to transfer funds.
Using a Hardware WalletHardware Wallet is a safer option compared to a software wallet. They minimize exposure by keeping the private key offline.
Be careful when publishing addressesPeople should be careful when publishing their encrypted addresses in the public domain (especially on social media sites) and should choose to use pseudonyms.
Choose a reputable walletIt is important to use a well-known wallet provider known for its security features and regular software updates to protect yourself from address poisoning and other attacks.
Regular updatesTo prevent address poisoning attacks, the wallet software must be continuously updated using the latest security fixes.
Implement WhitelistUse whitelists to limit transactions to reputable sources. Some wallets or services allow users to whitelist specific addresses that can send funds to their wallets.
Consider a multi-signature walletThe wallet that requires multiple private keys to approve transactions is called a multisig wallet. These wallets can provide additional protection by requiring multiple signatures to approve transactions.
Use blockchain analytics toolsTo detect potentially harmful behavior, people can use blockchain analytics tools to track and check incoming transactions. Sending seemingly trivial small amounts of cryptocurrency (dust) to multiple addresses is a common practice called dust. Analysts can detect potential by examining these dust trading patternspoisonous behavior.
Unused transaction output (UTXO) with a small amount of cryptocurrency is usually the result of dust transactions. Analysts can find addresses that may be poisoned by finding UTXOs related to dust transactions.
Report suspected attacksIndividuals should respond immediately when a suspected address poisoning attack occurs, contact the company that provides their encrypted wallets through official support channels and explain in detail what happened.
In addition, if the attack involves significant financial losses or malicious intentions, they may report the incident to the relevant law enforcement or regulatory authorities for further investigation and legal action. In order to reduce possible risks and safeguard the interests of individuals and groups in the cryptocurrency ecosystem, timely reporting is crucial.












