Author: Yohan Yun Source: cointelegraph Translation: Shan Oppa, Golden Finance
Since 2017, Lazarus Group has stolen more than $6 billion in cryptocurrency, becoming the most notorious hacker group in the industry.
Lazarus Group is not occasionally involved in the hacker world, it is often the main suspect in major cryptocurrency theft cases. The North Korean-backed group has become one of the most threatening hacker groups in the world by stealing billions of dollars from exchanges, tricking developers and bypassing the industry's most complex security measures.
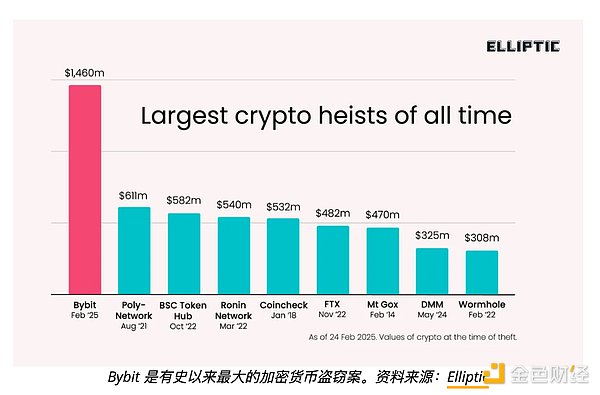
On February 21, 2025, it achieved its largest theft so far-stolen-1.4 billion USD from cryptocurrency exchange Bybit. Crypto Detective ZachXBT confirmed Lazarus as the main suspect after linking the Bybit attack with a $85 million hack on the Phémex exchange. He also linked the hacker attack to the vulnerability incidents in BingX and Poloniex, further adding evidence to the North Korean cyber army.
Lazarus Group has stolen approximately $6 billion from the cryptocurrency industry since 2017, according to security company Elliptic. A UN Security Council study notes that the stolen funds are believed to be used to fund North Korea's weapons program.
As one of the most active cybercrime organizations in history, the organization's alleged operators and means reveal a highly complex transnational operation designed to serve the North Korean regime. Who manipulates Lazarus behind the scenes? How did it successfully implement the Bybit hack? What other methods has it used to pose a persistent threat?
Lazarus Group Who's WhoThe U.S. Treasury Department claims that Lazarus is controlled by the North Korean Reconnaissance Bureau (RGB), the main intelligence agency of the North Korean regime. The FBI publicly named three suspected North Korean hackers as members of Lazarus (also known as APT38).
In September 2018, the FBI accused North Korea ofPark Jin Hyok, a suspected member of Lazarus, committed the most notorious cyber attack in history. Park Jin Hyuk allegedly worked for North Korean front company Chosun Expo Joint Venture, in connection with the 2014 Sony Pictures hack and the 2016 Bangladesh bank robbery ($81 million theft).
Park is also associated with the 2017 WannaCry 2.0 ransomware attack that paralyzes several hospitals, including the British Health Service (NHS). Investigators tracked Park and his accomplices through shared malware code, stolen credentials storage accounts, and proxy services that cover up North Korea and IP addresses. In February 2021, the U.S. Department of Justice announced that Jon Chang Hyok and Kim Il were included on their list of cyber criminal suspects prosecuted, who played an important role in some of the world's most destructive cyber invasions. The two were accused of working for the Lazarus Group, planning cyber finance crimes, stealing cryptocurrencies and laundering money for the regime.
Jon specializes in developing and spreading malicious cryptocurrency applications, penetrating exchanges and financial institutions, and carrying out large-scale theft. Kim is responsible for distributing malware, coordinating encryption-related thefts, and plotting a fake Marine Chain ICO.
How the biggest hacking incident of Lazarus Group happenedJust weeks before the Bybit hack, North Korean leader Kim Jong-un inspected a nuclear material production facility and called for the expansion of the country's nuclear arsenal to surpass current production plans, according to North Korean state media reports.
On February 15, the United States, South Korea and Japan issued a joint statement reiterating their commitment to North Korea's denuclearization. Pyongyang quickly refuted the statement on February 18, calling it "absurd" and vowed to strengthen its nuclear power again.
Three days later, the Lazarus Group took action again.
In the security circle, Lazarus's method of committing crimes is usually identified before the official investigation confirms his participation.
"In ByWithin minutes after bit's ETH was transferred out, I could confidently say privately that it had something to do with North Korea because their on-chain fingerprints and TTP (tactics, technology and procedures) were too unique. ” — Fantasy, the head of the investigation at Fairside Network, a crypto insurance company, said in an interview with Cointelegraph.
"They will split the ERC-20 assets into multiple wallets and immediately sell the tokens in a suboptimal manner, resulting in high transaction fees or slippages before transferring ETH to the newly created wallet in a large, neat amount. ”
In the Bybit attack, the hackers carefully planned a complex phishing attack to break through Bybit's security system and deceived the exchange to authorize the transfer of 401,000 Ethereum (ETH), worth $1.4 billion, to the wallet they controlled. According to analysis by blockchain forensics company Chainalysis, the attacker directly obtained access to the exchange assets by disguising as a fake version of the Bybit wallet management system.
After the funds were stolen, the hackers immediately initiated money laundering operations, spreading the assets to multiple intermediate wallets. Investigators at Chainalysis found that some of the stolen funds were converted into Bitcoin (BTC) and Dai (DAI), leveraging decentralized exchanges, cross-chain bridges, and KYC-free token exchange services, such as eXch, which refuses to freeze illegal funds associated with the attack despite the industry’s intervention in the Bybit hacking incident. eXch denies North Korea’s money laundering.
At present, a large portion of the stolen assets are still stored in multiple addresses, a common strategy used by North Korean affiliated hackers to circumvent strict tracking from regulators.
In addition, according to TRM Labs According to reports, North Korean hackers usually exchange stolen funds for Bitcoin. Bitcoin’s unused transaction output (UTXO) model further increases the difficulty of tracking, making forensic analysis much more complex than Ethereum’s account model. The Bitcoin network also has a variety of coin mixing services, and Lazarus frequently uses these tools to hide transaction traces.
Lazarus Group’s social engineering projectChainalysis says North Korean hackersIntensified its attacks on the cryptocurrency industry, stolen $1.34 billion through 47 attacks in 2024 - more than double the $660.5 million stolen in 2023.
The New York-based security company added that theft through private key leaks remains one of the biggest threats to the crypto ecosystem, accounting for 43.8% of all cryptocurrency hacking incidents in 2024. This approach has been used in several major attacks related to North Korea's Lazarus Group, such as the $305 million DMM Bitcoin attack and the $600 million Ronin hack.
While these high-profile thefts have dominated the headlines, North Korean hackers have mastered the skills of long-term fraud—a strategy that provides stable cash flow rather than relying on one-time surprises.
They target everyone, anything, any amount. Specifically, Lazarus focuses on these large and complex hacks such as Bybit, Phemex and Alphapo, but they also have smaller teams for low-value and more manual intensive work like malicious [or] fake recruitment interviews.
Microsoft Threat Intelligence has identified a North Korean threat team called "Sapphire Sleet" as a key player in cryptocurrency theft and corporate infiltration. The name continues Microsoft's weather-based classification, with "sleet" indicating a connection to North Korea. Besides that, the group is more well known as Bluenoroff, a subgroup of Lazarus.
They disguised themselves as venture capitalists and recruiters, luring victims into fake job interviews and investment scams, deploying malware to steal crypto wallets and financial data, making over $10 million in six months. North Korea also deploys thousands of IT personnel to Russia and other regions to obtain highly paid technical positions using AI-generated personal data and stolen identities. Once in, these hackers steal intellectual property, blackmail employers, and dump the proceeds into the regime. Microsoft's leaked North Korean database reveals fake resumes, fraudulent accounts and payment records, revealing a complex operation that uses AI-enhanced images, voice-changing software and identity theft to penetrate businesses around the world.
August 2024, ZachXBT reveals a network of 21 North Korean developers who earn $500,000 a month by embedding themselves into crypto startups.
In December 2024, a federal court in St. Louis unblocked the indictment against 14 North Korean nationals, accusing them of violating sanctions, wire fraud, money laundering and identity theft.
These people worked for North Korean-controlled companies Yanbian Silverstar and Volasys Silverstar, which operated in Russia, tricking companies into hiring them for remote work.
In six years, these workers have earned at least $88 million, some of which have been asked to earn $10,000 a month for the regime.
To date, North Korea's cyber warfare strategy remains one of the most complex and profitable actions in the world, allegedly transferring billions of dollars into the regime's weapons program. Despite the increasing scrutiny of law enforcement, intelligence agencies and blockchain investigators, the Lazarus Group and its sub-groups are constantly adapting to refine their tactics to evade detection and maintain illegal revenue streams.
With record crypto theft, deep penetration of global technology companies and an expanding network of IT operators, North Korea's network operations have become a long-term security threat. Multi-agency crackdowns in the United States, including federal prosecutions and millions of dollars in rewards, marks an intensified effort to undermine Pyongyang's financial pipeline. But as history has proven, Lazarus is ruthless; the threat posed by North Korean cyber army is far from over.












