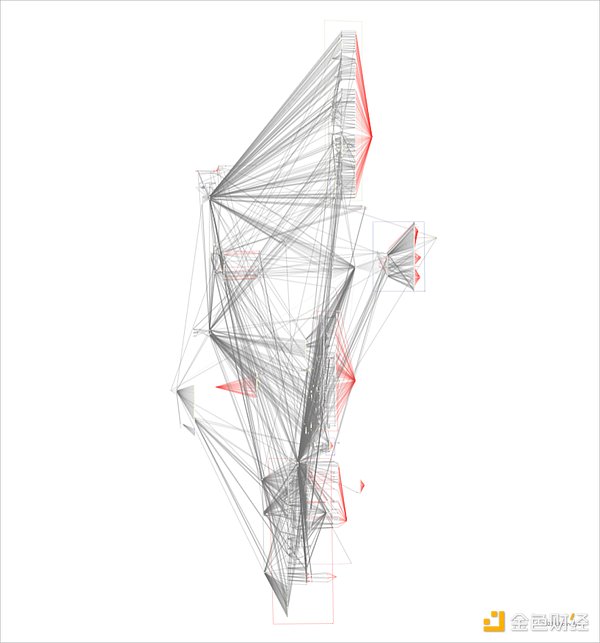
Source: Chainalysis; Compilation: Baishui, Golden Finance
On February 21, 2025, the famous cryptocurrency exchange Bybit encountered a major security breach, resulting in nearly US$1.5 billion worth of Ethereum (ETH) ) Loss. This incident is the largest theft in cryptocurrency history. Fortunately, Bybit is actively working with industry experts such as Chainalysis to track stolen assets. They also launched a recovery bounty program that offers up to 10% of the recovery amount to individuals who assist in recovering stolen cryptocurrencies.
In this blog, we will look at how vulnerabilities occur; attackers’ strategies, techniques and procedures (TTP) and their consistency with the Democratic People’s Republic of Korea (DPRK); and how Chainalysis Work with Bybit and law enforcement to help recover funds.
Bybit Vulnerability DetailsBybit hacking clearly reminds us that the means used by supportive cybercriminals, especially those related to North Korea, are constantly evolving. As we recently revealed in our 2025 Crypto Crime Report, North Korea-related hackers stole about $660.5 million in 2023. In 2024, that number increased to $1.34 billion in 47 incidents—the value of the stolen increased by 102.88%. Bybit hacking alone resulted in nearly $160 million more stolen than all the funds North Korea stolen throughout 2024.
This attack highlights a common trick used by North Korea: planning social engineering attacks and using complex money laundering methods to try to transfer stolen funds without being discovered. Funds from the Bybit vulnerability have also been integrated into addresses holding other attack funds known to be related to North Korea, further proof that actors are behind the latest incident.
The following is a step-by-step analysis of how the Bybit vulnerability is developed:
Initial intrusion through social engineering: Hackers gain access to the Bybit user interface by performing phishing attacks on cold wallet signers permissions, which leads them to sign malicious transactions, replacing Safe's multi-signature wallet implementation contract with malicious contracts.
Initiate an unauthorized transfer: During a routine transfer from Bybit's Ethereum cold wallet to hot wallet, the attacker intercepted the process. They managed to rerout about 401,000 ETH (worth nearly $1.5 billion at the time of the attack) to the address they controlled.
Asset dispersion through intermediary wallets: stolen assets are then transferred through a complex network of intermediary addresses. This decentralization is a common strategy to confuse traces and hinder blockchain analysts’ tracking efforts.
Convert and money laundering: Hackers exchange large amounts of stolen ETH for tokens such as BTC and DAI. They also use decentralized exchanges (DEXs), cross-chain bridges and instant exchange services without KYC to transfer assets across networks.
Keep funds stationary and strategic money laundering: a considerable portion of the stolen funds have been idle at various addresses, a deliberate method often used by North Korean hackers. By delaying money laundering operations, their goal is to undergo rigorous scrutiny immediately after such high-profile violations occur.
The Chainalysis Reactor chart below shows the complexity of money laundering operations to date: the network of intermediate addresses, token exchanges and cross-chain mobile is not only trying to cover up stolen funds, but also showing this attack. The profound impact of a wide range of crypto ecosystems.
Bybit Industry Cooperation After Hacking AttackAlthough Bybit's attack is very serious, the inherent transparency of blockchain technology is for malicious actors trying to whitewash stolen funds It is a major challenge. Each transaction is recorded on a public ledger, enabling authorities and cybersecurity companies to track and monitor illegal activities in real time.
The collaboration of crypto ecosystems is crucial to combating these threats. Bybit’s rapid response, including guarantees to cover customer losses and collaboration with blockchain forensic experts, reflects the industry’s commitment to mutual support and resilience. By integrating resources and intelligence, crypto communities can strengthen defenses against such complex cyber attacks and strive to create a safer digital financial environment.
We are working with global teams, clients and partners in the public and private sectors to support multiple avenues to seize and recover the attack. We have worked with industry contacts to help freeze over $40 million of funds stolen from Bybit and continue to work with public and private sector organizations to seize as much as possible. We will continue to provide the latest developments on this matter.










